Introduction — Why Cybersecurity Matters
Cyberspace is a complex environment composed of people, software, and services, and supported by the widespread distribution of information and communication technology (ICT) devices and networks. With the growth of IT in our organizations, creating a secure computing environment, enhanced trust and confidence in electronic transactions, software, services, devices, and networks has become a compelling priority. In today's world, protecting the information infrastructure and preserving the confidentiality, integrity, and availability of information in cyberspace is the need of the hour
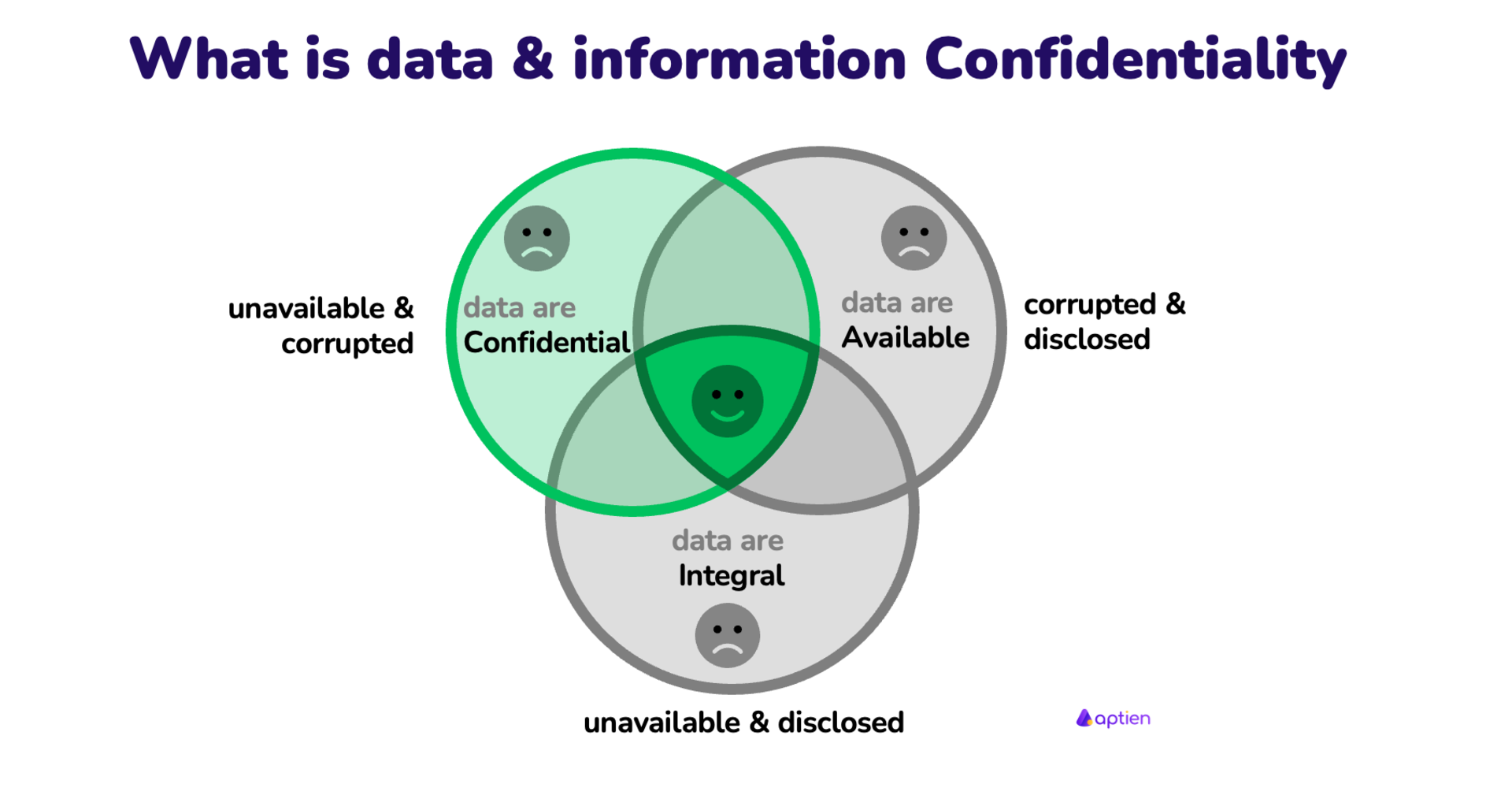
Confidentiality
Confidentiality is all about keeping sensitive information private. Only people who are supposed to see it should be able to, and that’s where a strong authentication process like multi-factor authentication comes into play.
Think financial records, medical records, or internal business plans. These need encryption, explicit file permissions, and consistent access controls to stay safe from prying eyes and accidental leaks. Security teams often layer in data classification protocols and endpoint protections as part of a holistic approach to prevent breaches that could lead to a security incident.
Integrity
Integrity means being able to trust your data. It shouldn’t be altered without permission; you need to know it’s accurate and complete. Businesses use tools like digital signatures, backup systems, and version control to ensure critical information, from invoices to patient records, stays exactly the way it should. To maintain integrity, cybersecurity experts also implement hashing, checksums, and tamper-evident controls, helping organizations detect unauthorized changes and respond to potential threats quickly.
Availability
Just as unauthorized users must be kept out of an organization’s data, data should be available to legitimate users whenever required. This means keeping systems, networks, and devices up and running.
All of these concepts are important to security professionals. However, these three concepts are grouped into a triad so information security professionals can consider their relationship, how they overlap, and how they oppose one another. Looking at the tension between the three legs of the triad can help security professionals determine their infosec priorities and processes.
The purpose of this module is to help you protect Aissel's information assets — our people, systems, and data — from accidental or intentional compromise. The company depends on secure IT to maintain trust, business continuity, and compliance with laws and internal policies.